Usually,when you deploy a service on a server you, will receive a lot of strange requests trying to discover the services running on your server or attacking it, for example trying to login in the ssh of your server.
Apart from having a strong password and the updated software, fail2ban mitigates this type of attacks blocking the ips that does this request.
How it works
Fail2ban reads the logs of various services that you can configure like ssh or Nginx, and looks for suspicious usages .
Once fail2ban detects incorrect login attempts, fail2ban blocks the ip using iptables
You can check the banned ips using this iptables command:
iptables -L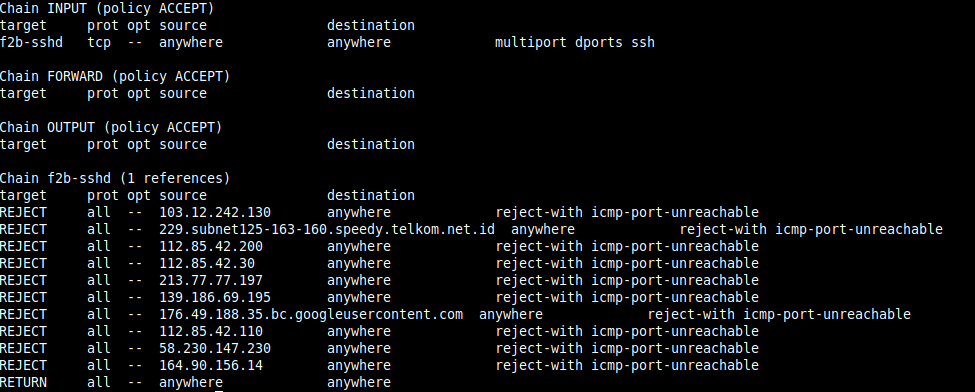
How to install and configure
You can install it with:
sudo apt-get install fail2banAfter this, you can configure the services that you want to monitor.
On the DEFAULT section there are the following parameters to configure:
- bantime: the seconds to ban the ip
- findtime: Window of time to check the intents of login
- maxretry: Number of intents
Tip
The time is specificatied in by default seconds, but you can add an m at the end to specificate minutes
After this you can see different sections to enable the services to monitor, for example:
[sshd]
# To use more aggressive sshd modes set filter parameter "mode" in jail.local:
# normal (default), ddos, extra or aggressive (combines all).
# See "tests/files/logs/sshd" or "filter.d/sshd.conf" for usage example and details.
#mode = normal
port = ssh
logpath = %(sshd_log)s
backend = %(sshd_backend)s
Finally you can add the tag enable = true to enable fail2ban to enable to monitor ssh
Deixa un comentari